Jhon the Ripper is a name that resonates deeply in both the cybersecurity and ethical hacking communities. Renowned as one of the most powerful password-cracking tools ever developed, Jhon the Ripper has become a staple for penetration testers, system administrators, and even curious tech enthusiasts. Its versatile and robust features make it a go-to solution for identifying weak passwords, improving security protocols, and uncovering vulnerabilities in networks. However, its widespread use has also sparked debates surrounding ethical boundaries and cybersecurity regulations.
What makes Jhon the Ripper truly extraordinary is its adaptability. With support for numerous password hash types and the ability to run on various operating systems like Linux, Windows, and macOS, the tool has cemented its place as an indispensable asset in the world of cybersecurity. From testing a single system’s defenses to auditing entire networks, Jhon the Ripper has been instrumental in fortifying digital infrastructures while raising awareness about the importance of strong passwords. Its open-source nature further contributes to its popularity, enabling developers to enhance its capabilities through constant innovation.
Yet, the story of Jhon the Ripper is not just about its technical prowess. It is also a tale of responsibility, ethical dilemmas, and the ongoing battle against cybercrime. As technology continues to evolve, so too does the role of tools like Jhon the Ripper in shaping the future of cybersecurity. This article delves into every aspect of this iconic tool, from its origins and functionality to its ethical implications and best practices. Let’s uncover the intricacies of Jhon the Ripper and understand why it remains a cornerstone in the cybersecurity landscape.
Read also:Harry Connick Jr Net Worth The Life And Success Of A Multitalented Artist
Table of Contents
- Biography and Origins
- What is Jhon the Ripper?
- How Does Jhon the Ripper Work?
- Key Features of Jhon the Ripper
- How Can You Use Jhon the Ripper?
- Types of Password Hashes Supported
- Why is Jhon the Ripper Important?
- Ethical Implications of Jhon the Ripper
- Jhon the Ripper vs. Other Tools
- Real-World Applications
- Common Errors and Solutions
- How to Avoid Misuse of Jhon the Ripper?
- Best Practices for Using Jhon the Ripper
- Future of Password Cracking Tools
- FAQs
Biography and Origins
Jhon the Ripper, abbreviated as JtR, is an open-source password-cracking tool that first emerged in the cybersecurity realm in 1996. Originally developed by Solar Designer (Alexander Peslyak), Jhon the Ripper quickly gained a reputation for being a versatile and efficient tool for password security auditing. Unlike its contemporaries, Jhon the Ripper's design was centered on speed, compatibility, and adaptability, allowing it to crack various types of password hashes.
Personal Details of Jhon the Ripper’s Creator
| Attribute | Details |
|---|---|
| Name | Alexander Peslyak (Solar Designer) |
| Profession | Cybersecurity Expert |
| Year Created | 1996 |
| Primary Purpose | Password Security Auditing |
| Open Source? | Yes |
With its roots in open-source development, Jhon the Ripper has continually evolved, thanks to contributions from a global community of developers. Its primary purpose is to identify weak passwords and enhance system security. Over the years, it has expanded its functionality to support a wide range of operating systems and password hash algorithms, making it one of the most comprehensive tools in its category.
What is Jhon the Ripper?
Jhon the Ripper is a password-cracking tool that serves dual purposes: ethical hacking and security auditing. It operates by testing various password combinations against a target's password hash to identify vulnerabilities. Designed for penetration testers and system administrators, the tool is lauded for its efficiency, speed, and customizability.
Who Uses Jhon the Ripper?
- System Administrators: For auditing password strength within their networks.
- Penetration Testers: To simulate attacks and assess vulnerabilities.
- Cybersecurity Researchers: For studying password hash algorithms and defenses.
- Developers: For improving security protocols and frameworks.
Despite its powerful capabilities, Jhon the Ripper is also a tool that requires ethical responsibility. Misuse can lead to significant repercussions, both legally and morally, making it crucial for users to adhere to ethical guidelines and legal regulations.
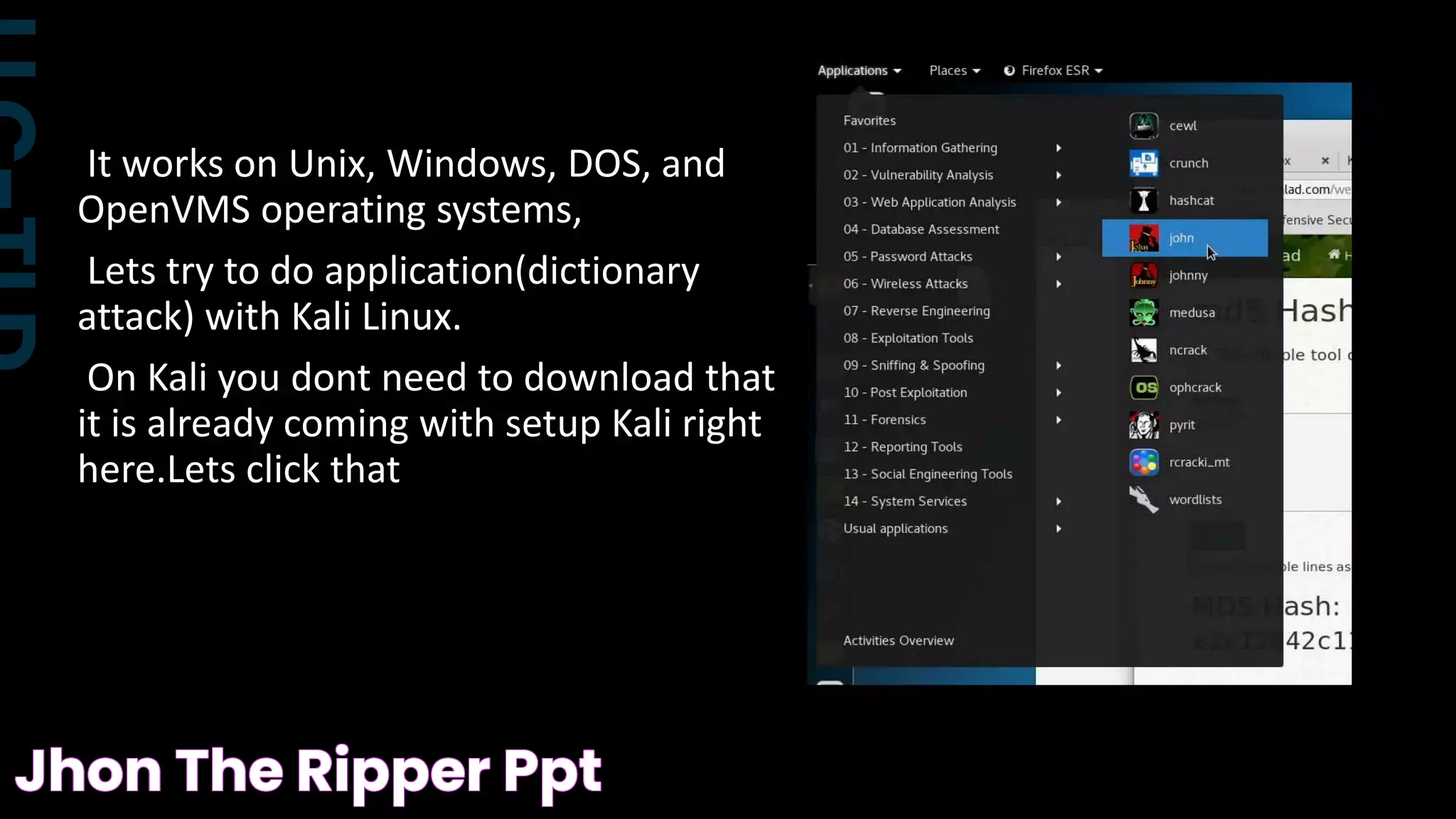
How Does Jhon the Ripper Work?
The core functionality of Jhon the Ripper lies in its ability to crack passwords using a variety of techniques. The tool operates by taking a password hash as input and attempting to reverse-engineer the original password through brute force, dictionary attacks, or hybrid methods. Let’s break down its process:
1. Hash Identification
Jhon the Ripper begins by identifying the type of hash used in a password. This step is crucial as it determines the algorithm JtR will use to decode the hash.
Read also:Ro And Kate Below Deck Insights Into Their Yachting Adventures
2. Attack Mode Selection
Users can select from multiple attack modes, including:
- Brute Force: Attempts every possible combination of characters.
- Dictionary Attack: Uses a predefined list of words or phrases.
- Hybrid Attack: Combines brute force and dictionary methods.
3. Cracking Process
Once the hash is identified and the attack mode is selected, Jhon the Ripper executes the cracking process. The time required varies depending on the complexity of the hash and the method used.
Continue reading for more insights on Jhon the Ripper’s key features, ethical implications, and real-world applications!